Michal Špaček: The Reason I Built “We Bleed” and How I Did It
This is an original guest post by PHP and security expert Michal Špaček.
It’s already been a month since we first heard about the Heartbleed Bug. For those of you who don’t know, Heartbleed is a critical security vulnerability in the OpenSSL library, which powers most of the encrypted communications across the Internet.
A lot has already been written about the vulnerability (remember – Heartbleed is not a virus!). But don’t worry – I didn’t write another article about how critical this bug is or when you’ll need to change your password again.
Instead, I’d like to share the results of a small weekend research project I’ve been working on.
It’s called We Bleed – a wordplay on Heartbleed and a Czech slang expression we use to describe someone who’s gotten sick from drinking too much. I’ve split the project into two parts. A front-facing page, which you can view here: heartbleed.michalspacek.cz. The backend isn’t public.
A few days after the bug was publicly disclosed, Robert David Graham of Errata Security updated his masscan tool so that it could check for the Heartbleed vulnerability. He scanned the entire Internet and found some 600,000 vulnerable servers worldwide.
After I read Graham’s report, I started to wonder how many servers in the Czech Republic were still vulnerable and wanted to conduct my own country-specific scan immediately. Despite being a newbie to scans of this volume, I do have some web application security knowledge. So, I started researching my options.
Two hours later, I’d already collected a list of more than 6.5M Czech IP addresses from RIPE I needed to scan and chosen a tool to check server vulnerability.
Luckily, there were already a lot of great tools circulating on the interwebs so I didn’t have to write the tool myself. In the end, I chose the same tool Mustafa Al-Bassam used to scan the Alexa top 10,000 sites. It’s suitable for scanning several sites in parallel, which would allow me to finish the scan of the vast Czech IPv4 space in a reasonable amount of time.
The power of this tool lies not only in the threaded scan, but also in the way it actually scans the servers. It uses a test case developed by David Chan of Mozilla and doesn’t exploit the server, so sensitive data isn’t leaked.
A week after the vulnerability was publicly disclosed, I was ready to run my first scan. It took 20 hours to scan 6.5M IP addresses on the HTTPS port. That made me a sad panda.

Five days later, after patching the tool to perform better for my use case (scanning network ranges, not single hosts) and tweaking the connection timeouts, I was able to scan the Czech IPv4 space in about 4 hours. Much better, but still not that impressive.
Later on, I switched to masscan (thanks, Rob!) to make a short list of IP addresses with open ports which I then fed to Mustafa Al-Bassam’s tool to check for vulnerability. Masscan made it possible to finish the scan in 2 hours. Nice, right?
Now wait, if masscan is able to scan the entire Internet in well under 10 minutes (3 minutes if you want to be exact), why did it take that long?
Here’s the thing, I was running the scans on virtualized hardware, which I rent for a few cents per hour.That means I’m able to scan the Czech IP space for less than 10 cents – beat that!
Unfortunately, I’m violating the usage policies of my current provider (even though I’m not exploiting any of the servers I scan), and I’ll have to find another provider soon. So, if you have any ideas about providers that would allow this type of scanning, I’d appreciate any suggestions.
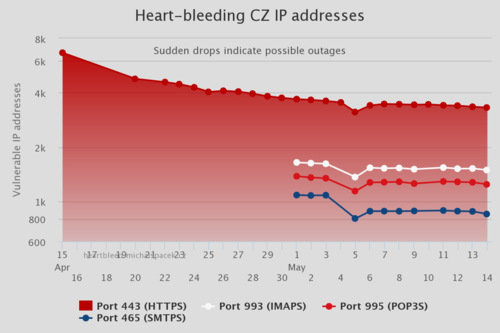
The Internet isn’t just made up of HTTPS and web servers. For example, I found several vulnerable network-attached storage devices. I also recently added scanning for vulnerable mail servers, which made the total number of unique vulnerable hosts increase again.
Now, I’m curiously waiting to see that number fall below 1K vulnerable hosts, but I wouldn’t hold my breath if I were you. Go check and patch your own servers and devices instead!
Note: I won’t be making my database public and will not exploit vulnerable servers, but if for whatever reason you’d like me to stop scanning your network, let me know. But I’d be happier if you whitelist my scanner to help me get more precise results! Just ask for the current IP address, thanks!

I build web applications, and I love web security. I speak at conferences and love real world examples. On a mission to show developers how to write secure code and why.
To find out more about his work, be sure to visit Michal’s website or follow him @spazef0rze.


